In Part 1 of this series, we covered the basics of setting up filtering for AAD Connect and the details of setting up domain filtering. In Part 2, we covered up the process of setting up OU filtering for AAD Connect. In Part 3, we’re going to cover setting up attribute filtering.
So you think want to setup attribute filtering, huh?
Well the first think I want to do is to encourage you to look back at part 2, and consider if you can meet your requirements with OU filtering. Filtering AAD Connect based on AD attributes is much more difficult to get working than OU based filtering.
One more time, if you can meet your requirement with OU filtering do that. If you cannot then you’ve probably done a poor job of Active Directory planning and deployment, so I would recommend you look at reorganizing your Active Directory so that you can use OU filtering.
Enough with the telling how hard it is, let’s get to the instructions
OK, here we go
There are several different ways to configure attribute based filtering. The recommended method is to use Inbound filtering since these settings will be kept after you upgrade your AAD Connect server. While you can use Outbound filtering, these settings WILL NOT be kept when you upgrade your AAD Connect server. What’s more, AAD Connect 1.1 includes an auto upgrade feature, so if you did a default deployment your AAD Connect server will update itself at some point without telling you. You’ve been warned.
Pick the attribute you want to use for filtering. In this example, I’ll be using extensionAttribute15. Users with this attribute set to DoNotSync will not be synced. Here it is important to note that not all attributes work! I figured out that extensionAttribute1 – extensionAttrubute10 DO NOT WORK for attribute filtering.
Select rule type Inbound Rules and select Add new rule.
Give the rule a name and a description.
For Connected System, select your on-premises Forrest (if both have the same name, the one with “– AAD” at the end is the wrong one).
For Connected System Object Type select user.
For Metaverse Object Type select person.
For Link Type select Join.
For Precedence select a number not in use by one of the other inbound rules. The actual number you use does not much matter, because no other existing rules do exactly the same thing as this one. If you have two rules that do the same thing, the one with the HIGHER precedence will win.
Hit Next to proceed to the Scoping filter screen.
On the scoping filter screen, select Add group.
Select Add clause.
Select extensionAttribute15 for Attribute, Equal for the Operator, and DoNotSync for the Value.
Hit Next to go to the Join Rules screen. Here is a good place to note that if you hit “Add clause” or “Add Group” again, you end up with extra commands that you cannot delete. You have to back out of this screen (and sometimes the whole rule creation wizard) to clear the extra lines.
Leave the join rules empty.
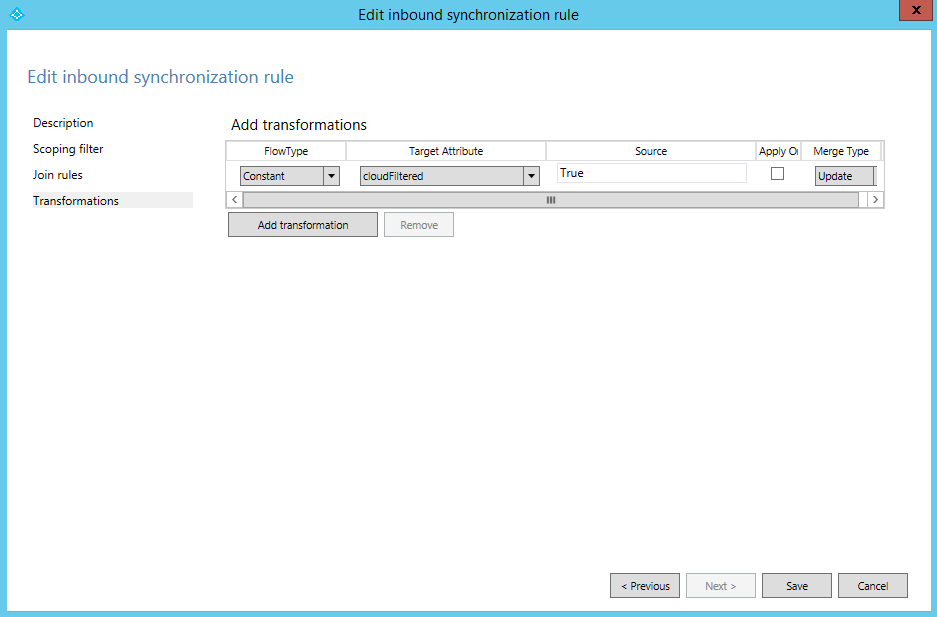
Hit Next to go to the Transformations screen.
Select Add Transformation.
Set FlowType to Constant.
Set Target Attribute to cloudFiltered.
Set Source to True.
Select Add (at the bottom) to save the rule.
Perform a full sync using the PowerShell command
Start-ADSyncCycle –PolicyType Initial
That’s it for the most basic sort of attribute filtering. In Part 4, I’m going to dive into some more advanced attribute filtering options.